AIoT in Smart Applications

Author(s)
Ruei-Hau HsuBiography
Ruei-Hau Hsu is the assistant professor in the department of computer science and engineering at National Sun Yat-sen university. He is also the supervisor of the Chinese Cryptology and Information Security Association.
Academy/University/Organization
National Sun Yat-sen university-
TAGS
-
Share this article
You are free to share this article under the Attribution 4.0 International license
- ENGINEERING & TECHNOLOGIES
- Text & Image
- October 18,2021
Next-generation mobile networks have launched a new era of intelligent communication and computation. Data exchange and application cross over all kinds of fields. Integration of intelligent communications and artificial intelligence makes the application of information technology more ubiquitous and environmentally aware. How to ensure that the security and privacy of digital assets of personnel/organizations can be guaranteed during the exchange and analysis of digital has become of utmost importance. Information security has become the key enabler in applying intelligent communications and computation. Prof. Ruei-Hau Hsu in the department of computer science and engineering at National Sun Yat-sen university leads intelligent communications and computation security labs to focus on the research of secure and privacy-preserving data sharing based on 5G multi-access edge computing for IoT, secure and privacy-preserving device-to-device communications in 5G, and privacy-preserving federated learning systems for artificial intelligence. The above three main research outcomes provide significant contributions for the security of intelligent communications and computation technologies.
Along with more complicated tasks/jobs and a high division of labor in life and work, people rely on computation and communication technologies to speed up the progress of diverse kinds of jobs. New types of communication and computation models, that is , enhanced mobile broadband (eMBB), massive machine-type communications (mMTC), and ultra-reliable and low latency communications (uRLLC), in 5G has been bringing the possibility of new applications into the internet-of-things (IoT). It also stimulates the exchange of various types of data in different fields in pace, coverage, and diversity. Thus, exploitation of digital data is being changed regarding the quantity and quality in a positive direction. Artificial intelligence/machine learning (AI/ML) as a killer technology in data science enables us to retrieve data from users/end devices, other than cloud platforms. In addition, in order to come up with the new requirements of new types of real-time IoT applications for higher transmission rates and lower latency, the development of information security technology for new types of communications and computations has become the key enabler.
The intelligent communication and computation security (ICCS) lab at National Sun Yat-sen university (NSYSU) led by Prof. Ruei-Hau Hsu aims at the research of security solutions for intelligent communication and computation. The research consists of two major directions. One is the research of security and privacy protection for IoT data sharing based on multi-access edge computing (MEC) in 5G. As shown in Fig. 1, IoT devices in the same proximity can exchange various kinds of data collected by diverse types of sensors by the assistance of the MEC platform for the IoT services in different fields. The procedure of data sharing achieves privacy-preservation and fine-grained access control without leaking the content of data and the context of data owners/consumers.
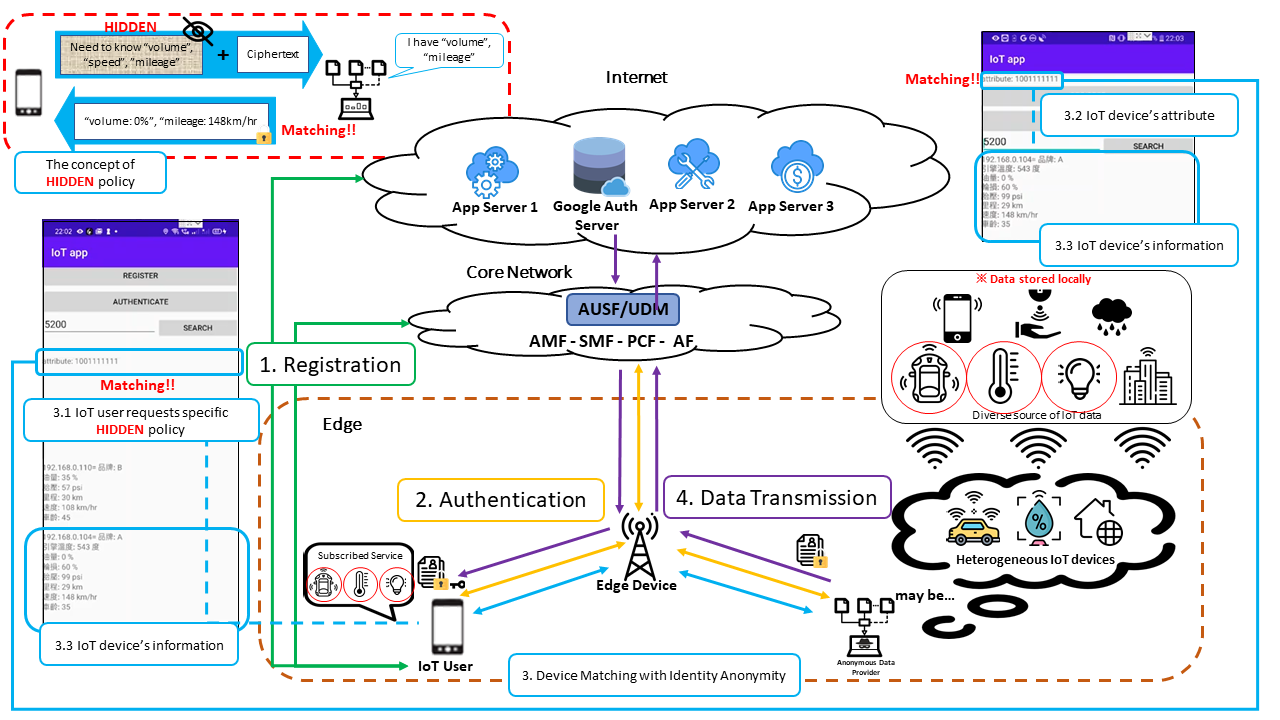
Figure 1. Privacy-preserving and fine-grained access controllable data sharing based on 5G multi-access edge computing for IoT
The other direction is the research of the security technology to support new types of device-to-device (D2D) communications for the expansion of IoT application scenarios, such as augmented reality/virtual reality (AR/VR), online social networks, public safety, and so on. Edge computing is able to provide the required assistance of security for the access control, confidentiality, and privacy protection during the establishment of D2D communications. As shown in Fig. 2, the emulated system for secure D2D communications is established using software-defined radio (SDR) equipment and the open source project, SRS-LTE, to emulate user equipment (UE), a.k.a. mobile phone, and base station (BS). The system allows us to discover UEs in the same proximity privately without exposing the identity and application/service information of each UE, and establishes session keys for the following D2D communications if a group of UEs is formed during the discovery phase.
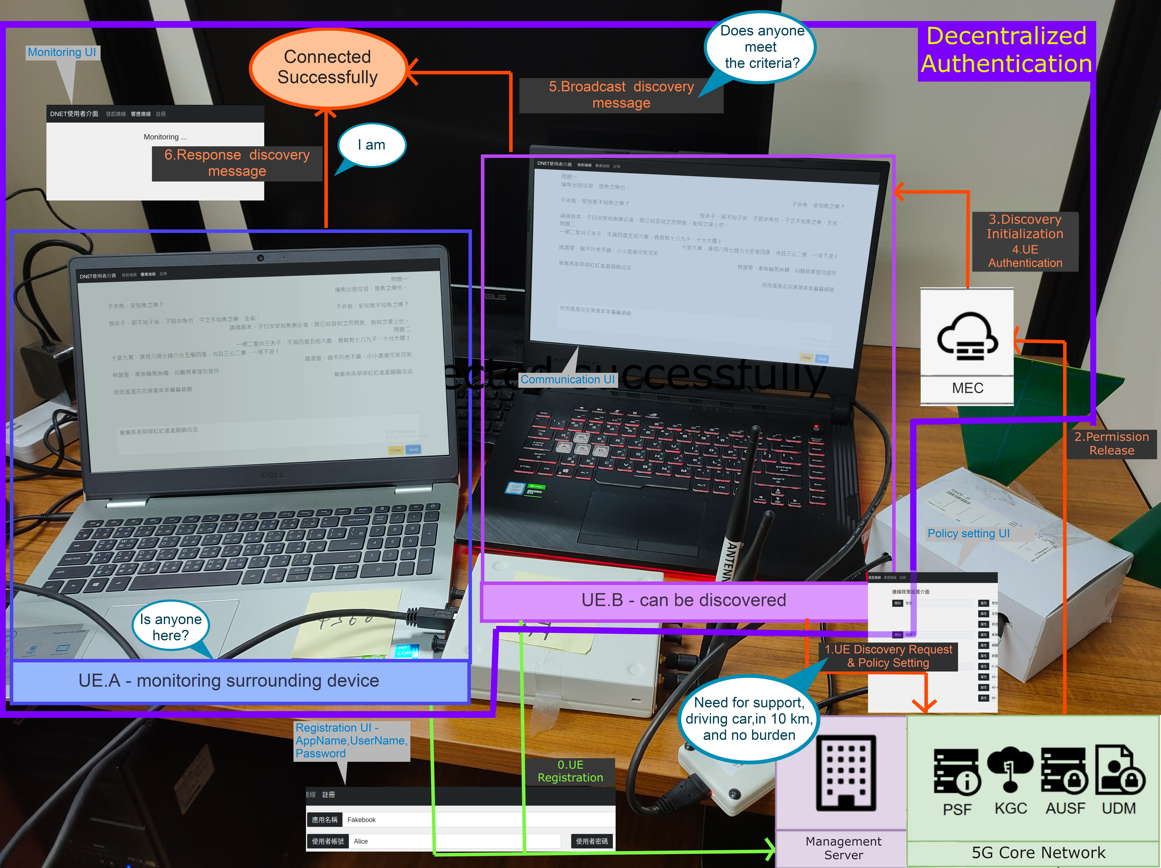
Figure 2. Secure device-to-device communications with privacy protection and fine-grained access control in 5G
When IoT data are exchanged frequently via the next-generation mobile communications technology, digital data can be analyzed and applied in real-time for various kinds of applications, such as smart transportation, smart cities, smart grids, smart factories, and so on. The future data science can combine higher diversity and a broader range of data for the analysis of dark data. The AI/ML models of dark data can be applied to all kinds of IoT applications/services. How to conceal sensitive data of individuals/organizations during the training of dark data is of utmost importance. Thus, the ICCS lab focuses on the development of privacy-preserving federated learning (PPFL) with access control for AI/ML as a service (AI/MLaaS). Figure 3 shows the developed system of PPFL, where data owners can contribute their data for the training of a global model without exposing their data content or any partial model by their data. The trained global model in PPFL is access controllable, where only the authorized model consumers can access it.
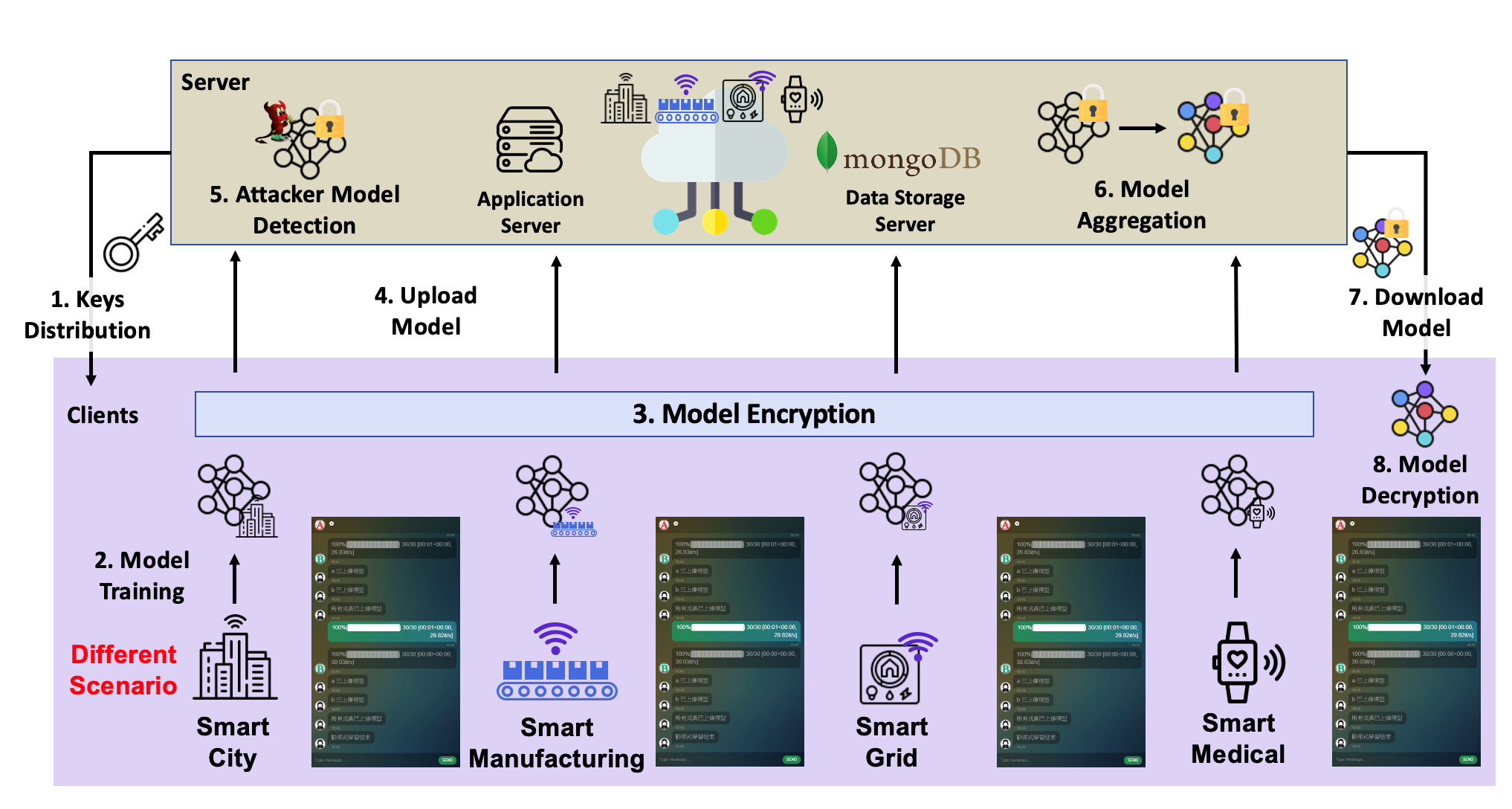
Figure 3. Privacy-preserving federated learning in AI
The research of secure intelligent communication and computation technologies paves the way to the next-generation applications of information technology/operational technology (IT/OT) for ubiquity, diversity, and cross-discipline. Conclusively, people’s digital assets, individual privacy, and safety can be guaranteed in the future world of the next-generation communications and computation technology.
STAY CONNECTED. SUBSCRIBE TO OUR NEWSLETTER.
Add your information below to receive daily updates.




