Post-Quantum Cryptography-Protecting Our Life From Quantum Computers with Modern Computers

Author(s)
Yi-Lang TsaiBiography
Tsai Yi-Lang, who serves in the National Center for High-Performance Computing of National Applied Research Laboratories, is currently the president of the Taiwan Branch of The Honeynet Project, Cloud Security Alliance and OWASP, and the vice president of CSCIS Greater China and North Asia. He is also the chairman of Taiwan Cyber Security Alliance, the chairman of the Taiwan Cyberspace and Security Strategy Development Association, and the supervisor of the Data Protection Association of the Republic of China. He actively invests in and pushes the promotion and research of detection, analysis, information security incident response and trapping technology in the field of information security in Taiwan. He has many international licenses such as RHCE, CCNA, CCAI, CEH, CHFI, ACIA, ITIL Foundation, ISO 27001 LAC, ISO 20000 LAC, BS10012 LAC, CSA STAR Auditing and CCSK. To date, he has written 35 books on computer information.
Academy/University/Organization
National Applied Research Laboratories-
TAGS
-
Share this article
You are free to share this article under the Attribution 4.0 International license
- ENGINEERING & TECHNOLOGIES
- Text & Image
- October 18,2021
In recent years, information security incidents have occurred frequently, affecting a wider range of aspects. At the same time, hackers' attack techniques are changing rapidly. Attacked targets are no longer limited to common operating systems or services, and even cover industrial control systems, webcams, portable devices, and so on, all of which may become hackers' targets. From the analysis of these major information security incidents, it can be known that hackers’ attack thinking is different from in the past, and it has begun to develop towards ways of obtaining benefits. Therefore, how to construct a perfect information security protection framework and cultivate information security talents has recently become a very important topic. Therefore, the National Center for High-Performance Computing developed the Cyber Defense eXercise (CDX) which started from practical needs. This cloud service platform provides information security attack/defense functions and also training for information security practical talents in order to strengthen the overall information security training energy in Taiwan.
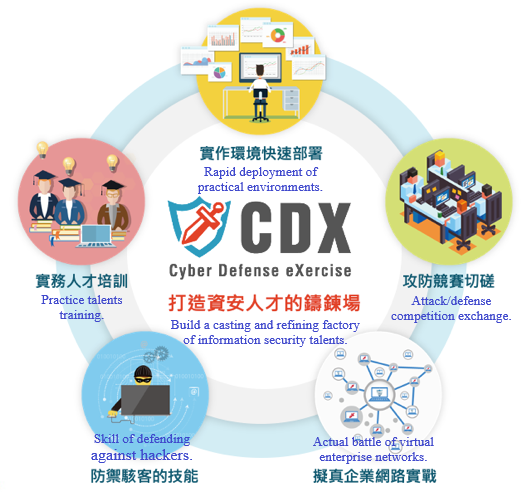
Information security threats have changed in response to the cloud service era and new information services. Faced with these current problems, there is still no complete talent training environment for the information security field. At present, most of the training programs are still at the stage of simply providing learning tools and software, and there is no one suitable training platform on which to learn about the events that happened in the past. By restoring the events, the information security attack and defense can be more authentic. This is important, as practical training for information security talent has become the most urgent need of the government, enterprises, and the information security service industry.
The Cyber Defense Exercise (CDX), independently developed by the National Center for High-Performance Computing, has the following six characteristics:
- Access control: The platform provides many information security tools. In order to avoid misuse by some people with nefarious purposes, the platform adopts a complete access control mechanism to manage users through account authentication and authority control. In order to avoid inadvertently affecting intranet users and other network services during the information security attack/defense drill, the cloud information security attack/defense platform is also matched with the exclusive isolated network environment to conduct strict access rule control.
- Rapid deployment: The platform is built with virtualization technology, and is equipped with a distributed storage mechanism for data access, and has the characteristics of high scalability for nodes, so the environment can be deployed more rapidly. Under the traditional architecture, it takes about 30 minutes to deploy a drill environment of the computer classroom, but it only takes about 90 seconds with the CDX platform. For the practical environment of information security that needs a large number of additions and deletions, rapid deployment really plays a very important role.
- Curriculum integration: The platform cooperates with the Information Security Incubation Program of the Ministry of Education to assist in the development of customized curriculum functions, and provides curriculum management and a slotting function. Users can plan and make units according to the content of curriculum modules, which can be bound to different curriculum themes. At the same time, it can also support the function of curriculum sharing, so that more teachers can use this curriculum for teaching promotion, and help to cultivate practical talents of information security in Taiwan, so as to meet the needs of information security talents in future industries.
- Competition environment: Through the platform's Vulnerability On Demand (VOD) function, the competition environment of individuals or organizations can be specially deployed, or an environment simulating enterprise network architecture can also be built. Virtualized information security equipment and external service system with vulnerabilities are provided. Meanwhile, the attack/defense mode of Red Team and Blue Team can be adopted to compete, so as to verify the strength of enterprise information security defense architecture and to help improve the practical technical ability of information security attack/defense.
- Vulnerability On-Demand: The platform can provide more than 200 types of vulnerability environments, including system vulnerabilities, application vulnerabilities, website and database vulnerabilities, logic and authority vulnerabilities, and so forth. Users can deploy their own environments for drills or training by means of Vulnerability On Demand (VOD), and provide a variety of information security tools and environments so that platform users can use them quickly without spending time looking for and installing them.
- Information security teaching materials: The teaching materials cover more than 12 types of information security technologies, including penetration testing, vulnerability scanning, malware analysis, network packet analysis, website security, and digital forensics, and can be matched with curriculum functions to build the practical operating environment required for training, so as to help trainees improve their technical skills in information security practice, and apply the learned technologies to daily work and maintenance, so as to strengthen the energy of information security incident handling and maintenance.
The new generation cyber range can be used for learning and analyzing information security events. Through Exploit Code or PoC (Proof of Concept) programs from the Internet, it can reproduce the vulnerability existing in the system over years, so as to master the methods and communication protocols adopted by network attacks, which will help cope with the information security technology energy needed under the threat of the new generation of information security, and learn the protection energy needed to build enterprises.
STAY CONNECTED. SUBSCRIBE TO OUR NEWSLETTER.
Add your information below to receive daily updates.