Development of in vitro Brain Models as a Platform for Neurodegenerative Disease Understanding and Drug Discovery

Author(s)
Chun-I FanBiography
Chun-I Fan has been a Distinguished Professor of the Department of Computer Science and Engineering and the Dean of the College of Engineering at National Sun Yat-sen University. Moreover, he is the Director of the Information Security Research Center at National Sun Yat-sen University and Chairman of the Chinese Cryptology and Information Security Association. From 2011 to 2020, he received the Outstanding Faculty Research Award in Academic Research of National Sun Yat-sen University for 10 years. Furthermore, he has won the IEEE Tainan Section Outstanding Technical Achievement Award. His research interests include Applied Cryptology, Information and Communication Security, and AI Security.
Academy/University/Organization
National Sun Yat-sen UniversitySource
https://ieeexplore.ieee.org/document/8772129-
TAGS
-
Share this article
You are free to share this article under the Attribution 4.0 International license
- ENGINEERING & TECHNOLOGIES
- Text & Image
- October 18,2021
Due to the fact that the higher density of mobile devices is expected, the fifth generation (5G) mobile networks introduce small cell networks (SCNs) to prevent exhausting radio resources. SCNs improve radio spectrum utilization by deploying more base stations (BSs) in the networks. Authenticated key exchange (AKE) is essential to ensure entity authentication and confidentiality in mobile communications. Besides, user anonymity is required to guarantee the footprints of mobile communications being concealed. However, AKE with user anonymity may dramatically increase the latency of communications in total due to several times more frequency in SCNs. The increase of latency will be more serious when an AKE protocol supports user anonymity, where traceability and revocability to users are necessary. Thus, this work presents a secure region-based handover scheme (ReHand) with user anonymity and fast revocation for SCNs. ReHand greatly reduces the communication latency when user equipment (UE) roams between small cells within the region of a macro BS, that is, eNB, and the computation costs due to the employment of symmetry-based cryptographic operations. Compared to the three related prior arts, ReHand dramatically reduces the latency from 82.92% to 99.99% by region-based secure handover. Nevertheless, this work demonstrates the security of ReHand by theoretically formal proofs.
The three major scenarios of the 5th Generation Mobile Networks (5G) defined based on 3GPP are illustrated in Figure 1, which are Enhanced Mobile Broadband (eMBB), Ultra-Reliable and Low Latency Communications (URLLC), and Massive Machine Type Communications (mMTC). At the same time, for the applications of IoT technology and artificial intelligence, new types of communication methods, computation models, and network models are also proposed to support more innovative applications. Among them, the 5G millimeter-wave wireless communication technology is one of the major differences between 4G and 5G, and is also the key technology that can bring the 5G bandwidth into full play. Since the transmission distance of the millimeter wave is shorter than that of the original cellular network, in order to fully cover the same area/space, the base stations of the mobile network need to be laid out through small cells that are more densely distributed and have a smaller transmission range, which shall significantly increase the frequency of switching between base stations for mobile devices and shall also increase the transmission service latency. The said "switching between base stations" is the "handover mechanism" mentioned in this study, which means that in a mobile network environment where the user keeps moving, the user's device should transfer its connection from the original cell to the nearest cell to the user's current location to maintain the quality of communication.
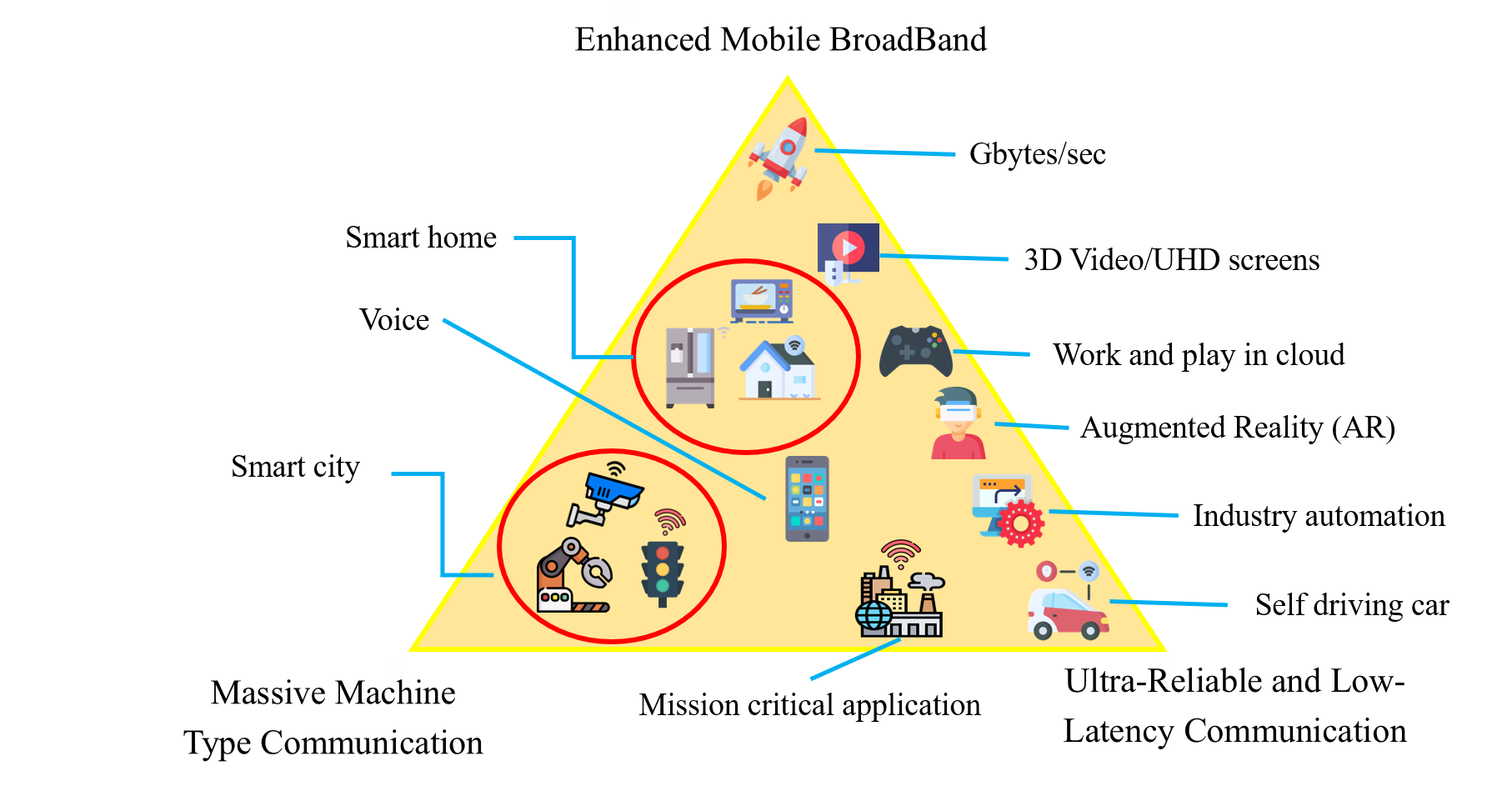
Figure 1. Three major scenarios for 5G applications
This study proposes an anonymous authentication and key exchange protocol applicable to the small cell networks/ultra-dense networks as well as the corresponding rapid handover mechanism; the system structure of which is illustrated in Figure 2. This study adopts the regional symmetry key deployment strategy and accumulated one-way hash functions in the design of the security protocol, which not only possesses the characteristics of anonymous authentication but also supports the mechanisms of rapid handover and user revocation. In addition to features such as anonymity, rapid handover, and user revocation, this study also employs formal security analysis to prove its security. Regardless of whether it is a man-in-the-middle attack or a replay attack, it can be resisted without leaking the user’s information so as to achieve the purposes of secure and rapid handovers and protection of the user’s privacy.
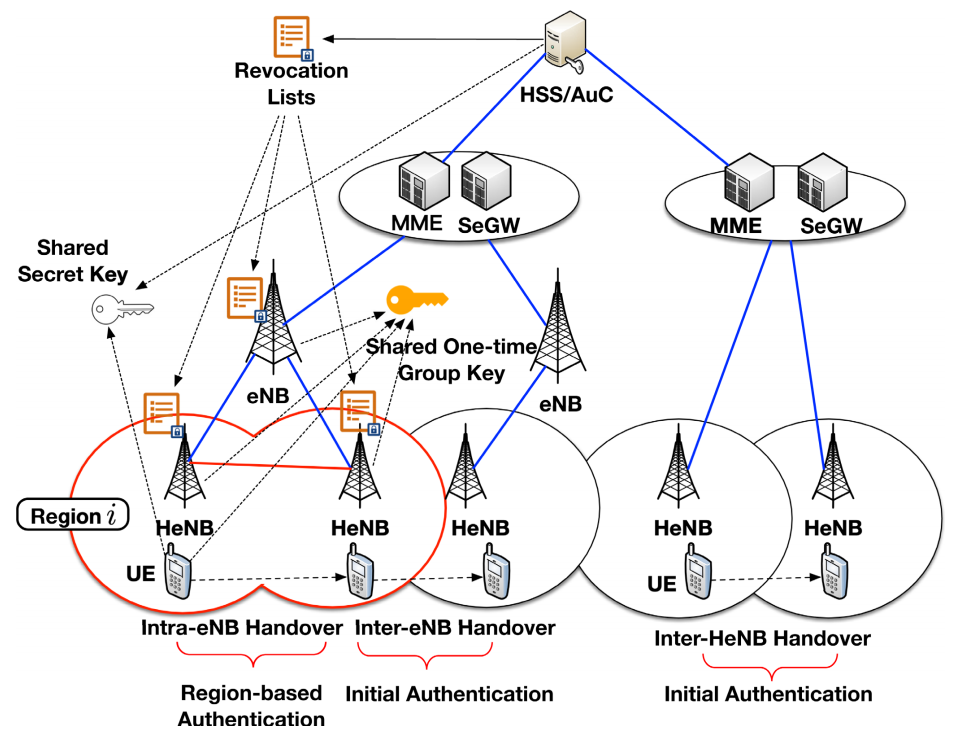
Figure 2. The system model of small cell networks in 5G
In terms of its performance, this work surpasses all currently known authentication and key exchange protocols with a rapid handover mechanism. Compared with the current fastest secure handover mechanism, the proposed mechanism can save up to 80% of the total execution time. In regard to the cost of deployment, with a cryptographic system that completely uses symmetric-key algorithms, the proposed method demonstrates significantly high efficiency in key encryption/decryption. Due to the frequent execution of the handover mechanism in the communication environment, a substantial reduction in the total execution time of a single handover shall have a very significant effect on the overall efficiency, which is also suitable to be used on IoT devices with limited computational capacity. Moreover, it can also avoid the maintenance cost of the public key infrastructure required by the use of public-key algorithms.
With the frequent occurrence of information security incidents and their worsening impacts, related issues have gained increasing importance in recent years. The devices used nowadays, including mobile phones, tablets, computers, those in vehicles and even homes, are increasingly relying on the assistance of various smart devices, which makes daily life inseparable from information technologies. Thus, the security of these technological devices shall directly connect to the safety and corresponding protection of our lives and property. Recently, major telecommunications companies are also actively engaging in the deployment of the 5th Generation communications technologies such as Smart City, intelligent transportation, building construction, agriculture and logistics, and so on, which implies that the safety/security of these links is a very important challenge to the actual applications of the 5th Generation mobile telecommunications technologies in the future. Let us do our part for information security and create a more convenient and safer 5G life!
STAY CONNECTED. SUBSCRIBE TO OUR NEWSLETTER.
Add your information below to receive daily updates.




