Beyond Moore's Law – the “More Than Moore” Monolithic 3DIC Technology

Author(s)
Hsing-Yen AnnBiography
Hsing-Yen Ann received his Ph.D. degree in computer science and engineering from National Sun Yat-sen University. He is currently an associate researcher in National Center for High-Performance Computing, NARLabs. His works include research projects for detecting, analyzing the behaviors of the malwares, and help to the incident responses. His research interests also include big data analysis and the architectures of big databases.
Academy/University/Organization
National Applied Research Laboratories-
TAGS
-
Share this article
You are free to share this article under the Attribution 4.0 International license
- ENGINEERING & TECHNOLOGIES
- Text & Image
- October 19,2021
The Science Park Information Sharing and Analysis Center (SP-ISAC) provides the information security personnel of the Park with the ability to grasp the latest attack tactics and quickly propose countermeasures so as to achieve the goals of early warning, better coordination, and instant response. Information security threat analysis and information sharing are conducted with de-identification and the exclusion of business secrets, which also facilitates rapid response to avoid major information security attacks, carries out information security joint defense between high-tech industries in the park and government agencies, and strengthens and enhances information security awareness.
In order to promote the threat intelligence exchange of key information infrastructures in high-tech parks and to enhance information security protection, the Ministry of Science and Technology entrusted the National Center for High-performance Computing, National Applied Research Laboratories (NCHC, NARLabs) to plan and build the Science Park Information Sharing and Analysis Center (hereinafter referred to as SP-ISAC). Through the construction of an information platform, information collection and analysis, information security education and training, etc., the information security personnel of the park industries can grasp the latest attack tactics and quickly propose countermeasures so as to achieve the goals of early warning, better coordination, and emergency response.
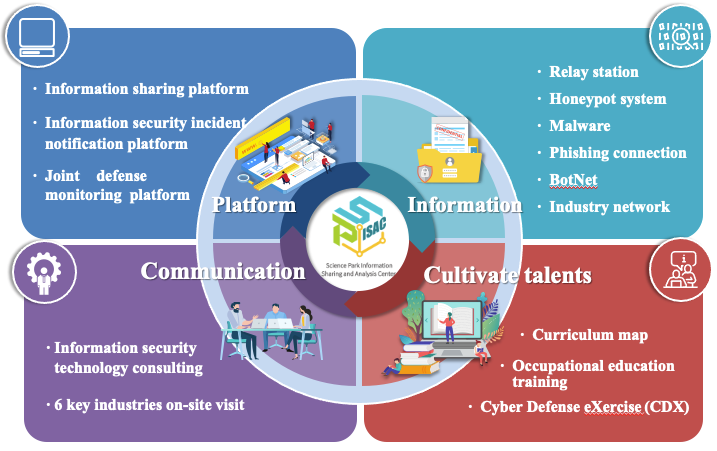
Figure 1. Key Tasks of SP-ISAC
1. Information platform
SP-ISAC has built an automatic threat intelligence exchange system, and through STIX (Structured Threat Information Expression) information standardization and the sharing and exchange mechanism of TAXII (Trusted Automated Exchange of Indicator Information) system automation, connects with the National Information Sharing and Analysis Center (N-ISAC), so as to achieve real-time information sharing and early warning, quickly notifies information security incidents and shortens the response time, and thereby enhances the overall information security protection capability of science park industries.
2. Information Feedback and Threat Analysis
High-tech parks contribute 14% of Taiwan's gross domestic product (GDP) and play a key role in the national economy. In recent years, Taiwan has often been targeted by hacker groups in Advanced Persistent Threat Attacks (APT Attacks). From time to time, hackers use phishing emails and customize malicious programs (such as Lockbit, Hello Kitty, and other malicious software) to extort or attack.
Therefore, when science park industries find that there is a suspected incident of information security breach, or that there are information security threats and weaknesses, SP-ISAC will provide a variety of contact methods as an information security feedback channel, provide timely technical support and assist in handling information security incidents, and at the same time use de-identification and exclusion of business secrets to conduct information security threat analysis and information sharing, so as to facilitate rapid response to avoid major information security attacks, carry out information security joint defense between high-tech industries in the park and government agencies, and strengthen and enhance information security awareness.
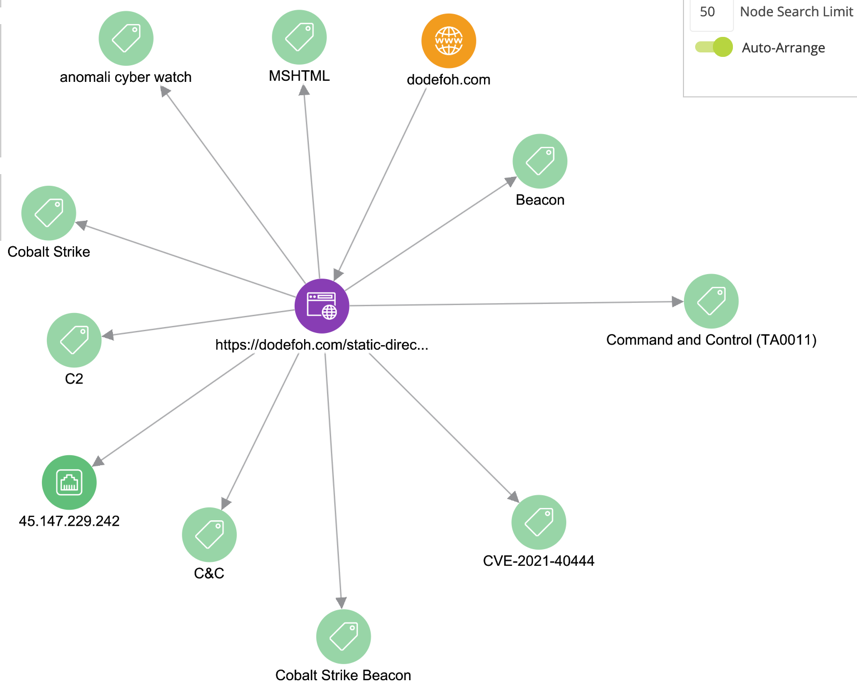
Figure 2. Threat Information Analysis of ATP Attack Organization
3. Education/Training of information security practice
The SP-ISAC team plans to organize education and training courses of information security technology for information security staff of member industries in the Science Parks. Based on the concept of information security attack/defense warfare, through the scenario simulation of Red Army attack and Blue Team defense, and by incorporating the elements of information security incident investigation, it plans practical curriculum content from basic to advanced levels so that park industries can have basic information security contingency ability when encountering information security incidents and cooperating with third-party information security partners for information security planning. In this way, it can upgrade the information security specialty of high-tech parks, narrow the gap between industrial information security talents, and strengthen the awareness of information security protection. Since the service started in 2018, SP-ISAC has handled 56 training curriculums on information security, and has assisted park industries in cultivating 1,754 information security talents.
As the promoter of protection of national key infrastructures in the high-tech field, SP-ISAC established the defense framework covering advance threat prevention, response during the event, and disposal afterwards. It assists the internal information security personnel in the enterprises to defend against information security threats and eliminate information security incidents, and serves as the best information security partner for high-tech park industries. When the industries in the science parks encounter information security incidents, SP-ISAC can assist as the information security backing of industries and guard the daily information security of the park.
STAY CONNECTED. SUBSCRIBE TO OUR NEWSLETTER.
Add your information below to receive daily updates.




